In today’s digital world, cyber security governance plays a huge role in detecting the threats before they occur. One of the crucial steps is to perform web application security tests during the testing phase. Public-facing websites, which are easily accessible, are the biggest target these days. It is very difficult to save an application from the hackers. However, in this blog we have mentioned some of the best practices that can be implemented to minimize the chances and impact of such breaches.
Keeping that in mind, It’s the developer’s job to ensure that certain security standards and practices are followed during the development phase to ensure protection from high-risk vulnerabilities. A code review process during the development stage, before the code is released for testing, can play a significant role in application security. There are various automated tools available, that follow pre-defined rules, to do the code review and be a part of the process.
Impact of Security Breaches
Trust is a crucial aspect for consumers to do business with a company; data breaches act like a roadblock in such relationships. Check out the trends below to understand the financial loss that occurred in 2017 due to data breaches.
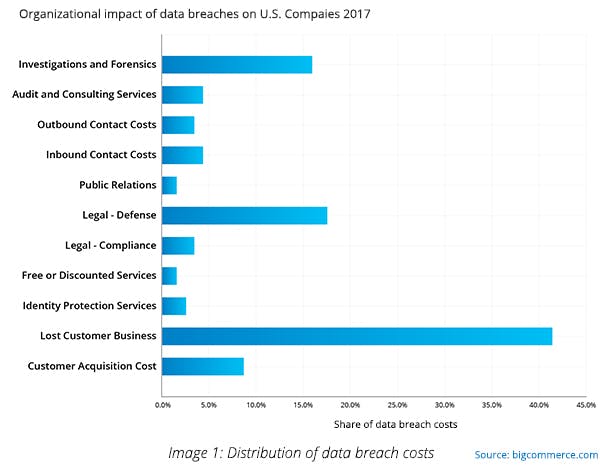
According to Kaspersky, in 2018, this cost has risen to $1.41 million. In 2019, over 4000 data breaches have been reported with financial damage of approx. $675,000 million. In 2016, Yahoo! announced that it was the victim of the biggest hack in history. Around 500 million users’ data was stolen by the hackers having real names, email addresses, date of birth, and telephone numbers. In 2015, it was found that somebody was selling that data on the dark web. The breach also impacted Verizon Communication’s plan of acquiring Yahoo! when they drastically reduced the price by $350 million. In 2018, it was reported that over 500 million user accounts were affected.
To ensure that the applications are secure from the hackers, it is essential to set security goals from the app development phase. The three important application security goals — Confidentiality, Integrity, and Availability — are explained in detail below:
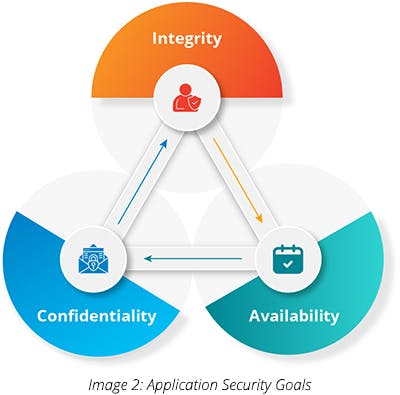
Confidentiality ensures that the information present in the application is accessible to the user for whom it is intended. Any unauthorized access to information will violate this goal.
Integrity means that the authenticity of information is retained without any alteration. In case a malicious user changes the information, it may negatively impact the decisions made by the enterprise.
Availability means that the authorized users must have uninterrupted access to information. A malicious user may violate this goal by executing attacks like denial of service, which may bring down the server and make the whole website unavailable.
Let’s discuss how to ensure that the above goals are achieved. Below are a few principles that can help a developer to do secure coding while developing the application.
4 Principles to Achieve Application Security Goals
1. Authentication - A way to identify the user who they claim to be. Make authentication more secure by enforcing the following policies:
- Password policy – Password length should be more than 8 characters and it must include special characters like $, #, etc. Change the password well before it expires and do not reuse the previous passwords.
- Account lockout - Implement account lockout for failed login attempts to guard against a brute-force attack.
- Test ‘Forgot my password’ functionality thoroughly - Application should only send the password to the registered email address. It should not ask the user to enter an email address to send the password.
- POST method should be preferred over GET method – Whenever an application wants to pass sensitive data, always enforce the POST method in the server-side and client-side in web application. Using the GET method can expose the browser’s history, web logs, and referrers.
2. Authorization: Authenticated users should be allowed to access the intended resources within an access-control mechanism. To ensure correct authorization, organizations should consider below-mentioned points:
- Least privilege – Not everyone should have access to everything. Create separate users with specific privileges that allow them to access only the intended areas of the system. This practice will define the roles in such a way that even if a malicious user is able to get the credentials, they will not have access beyond a point.
- Access/context verification – Every user must be verified before they can access a certain page/function. It must also verify whether the user is allowed to perform certain action within the given context or not.
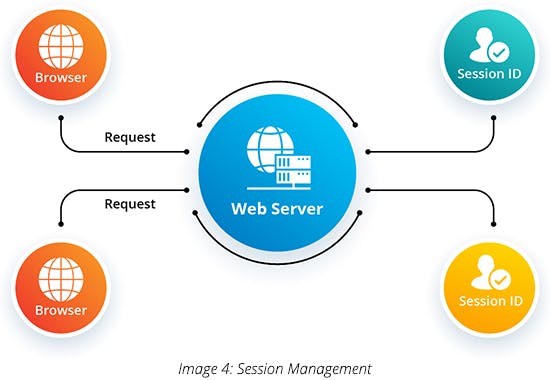
3. Session Management: To track each user state while accessing the web application an organization need to do the following:
- Re-using session information - With SSO (single sign-on) and multiple integrated applications, the system should maintain the authentication cookie in a way that the users are allowed to access all the applications without logging in again. For that, store a “SessionID” at the server-side.
- Enforce session expiration policy – Define a duration for each session. In case a malicious user takes over a session, it will only last till the session expires.
4. Data Validation: Any data collected from the client should be sanitized before being sent to the server. Validate the data at the server-side to disallow a malicious user from bypassing the client and sending requests directly to the server. Mechanisms that require to be followed to validate the data:
- Blacklist and whitelist – Filter the data on the basis of the blacklist and whitelist (that contains the characters that are not allowed).
- User input must be validated before it is used in SQL commands – If the data input is not validated, a malicious user may carry out SQL injection attacks.
- User input must be validated before it is sent back to the client (browser) -Failure to do so would lead to XSS injection (persistent and reflected) attacks on the website.
- User input must be validated before it is used in system commands –Eval function must be written very carefully when executing OS-level commands. For example, the Ping program should only accept the IP addresses and must ignore anything after that.
- Validate data length before it is written to a variable – In this case, program copies an input buffer to an output buffer without verifying its size. The program should verify the length of the input buffer and ensure that it must be of the same size as the output buffer, which may otherwise lead to a buffer overflow.
The policies and standards mentioned above must be enforced at the code level so that the developers can implement them during the application development phase. The code should be reviewed in a way to ensure that it does not allow the application users to break these policies. Cyber security governance must monitor the policies and change them as and when needed.
If an enterprise wants to prevent any financial damage, they must monitor their internal security and implement quick incident breaches. It is crucial to implement cyber security governance at an organizational level since it is not just an IT issue but a company’s issue. Following processes and procedures must be a part of the enterprise cyber security governance and should be implemented rigorously at any functional level of the organization:
- Create data policies
- Train and educate the teams
- Use encryption wherever possible
- Better user authorization
- Track and monitor the usage
- Practice patch management
- Carry out system audit regularly
- Backup and restore the policies
Considering the above scenarios, organizations must follow preventive measures to stop such security breaches. They should limit the data access by limiting the number of users and enable auditing in the database server to track the specific events that may be responsible for modifying data in any form.
Each employee must be trained to be aware of the situations that may lead to data breaches – for example, opening suspicious emails, clicking on suspicious links which leads to phishing attacks, etc. Update the software regularly and apply the recommended patches. Set up a team to respond to such attacks and have a security-breach plan in place.
You can also check out other blogs to understand High Risk Vulnerabilities in ASP.Net , PHP and about Cross site forgery.




